US Claims Major DDoS-For-Hire Takedown, But Some ‘Seized’ Sites Still Load Online
U.S. Officials Seize Domains Linked to DDoS-For-Hire Websites, But Some Remain Online
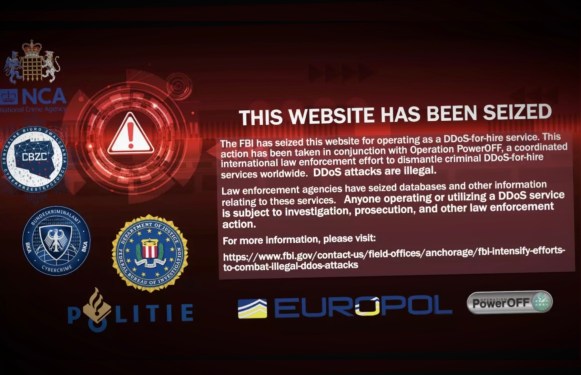
In a significant effort to combat the growing threat of distributed-denial-of-service (DDoS) attacks, U.S. officials have announced the seizure of 48 domains linked to some of the world’s leading DDoS booter platforms. However, an investigation by TechCrunch has revealed that several of these seized sites continue to load as normal, raising questions about the effectiveness of this operation.
The Operation
As part of a joint effort between the U.S. Department of Justice (DOJ), the UK’s National Crime Agency (NCA), Dutch police, and Europol, known as "Operation PowerOFF," 48 domains associated with DDoS booter services were seized. These services, often masquerading as bandwidth stress-testing tools, allow individuals to carry out DDoS attacks designed to overwhelm websites and networks.
The Targets
According to the DOJ, these booter sites have been involved in attacks against a wide range of victims, including educational institutions, government agencies, and gaming platforms. Europol noted that one of the seized sites has been used to carry out over 30 million attacks. The operation aimed to disrupt the activities of these DDoS-for-hire services and bring those responsible to justice.
The Arrests
In addition to the domain seizures, law enforcement officials have arrested seven individuals who allegedly oversaw the DDoS booter services. In the U.S., six individuals have been charged with crimes related to their involvement in these operations:
- John M. Dobbs
- Jeremiah Sam Evans
- Angel Manuel Colon Jr.
- Shamar Shattock
- Cory Anthony Palmer
- Joshua Laing
The Investigation Continues
Despite the arrests and domain seizures, TechCrunch found that at least eight of the sites supposedly seized by U.S. prosecutors continue to load as normal. It is unclear why these sites remain operational.
DOJ spokesperson Thom Mrozek told TechCrunch that there was a delay in getting the FBI splash-pages. "We are working with the registries to make this happen," he said. Mrozek added that while some sites may still be online, they are no longer functioning and cannot be used to launch attacks.
The UK’s Contribution
The U.K.’s NCA announced that it has arrested an 18-year-old man in Devon who is suspected of being an administrator of one of the seized sites. The NCA also stated that customer data from all of the DDoS booter sites was obtained and will be analyzed by law enforcement.
Admins and Users Based in the UK
The NCA warned that admins and users based in the U.K. will be visited by the National Crime Agency or police in the coming months. This emphasizes the ongoing efforts to disrupt and dismantle these DDoS-for-hire services.
Conclusion
The takedown of 48 domains linked to DDoS booter platforms is a significant step towards combating the threat of DDoS attacks. However, the fact that some of these sites remain online raises questions about the effectiveness of this operation. The investigation continues, and it remains to be seen how successful this effort will ultimately be in disrupting these malicious services.
Related Stories

